Kaspersky’s detection systems discovered an average of 500,000 malicious files per day in 2025, marking a 7% increase compared to the previous year. Certain types of threats saw growth globally – there was a 59% surge in password stealer detections, a 51% growth in spyware detections and a 6% growth in backdoor detections compared to 2024.
500,000 malicious files per day were discovered on average by Kaspersky's detection systems in 2025
These findings are part of the Kaspersky Security Bulletin series where we review the key cybersecurity trends of the past year.
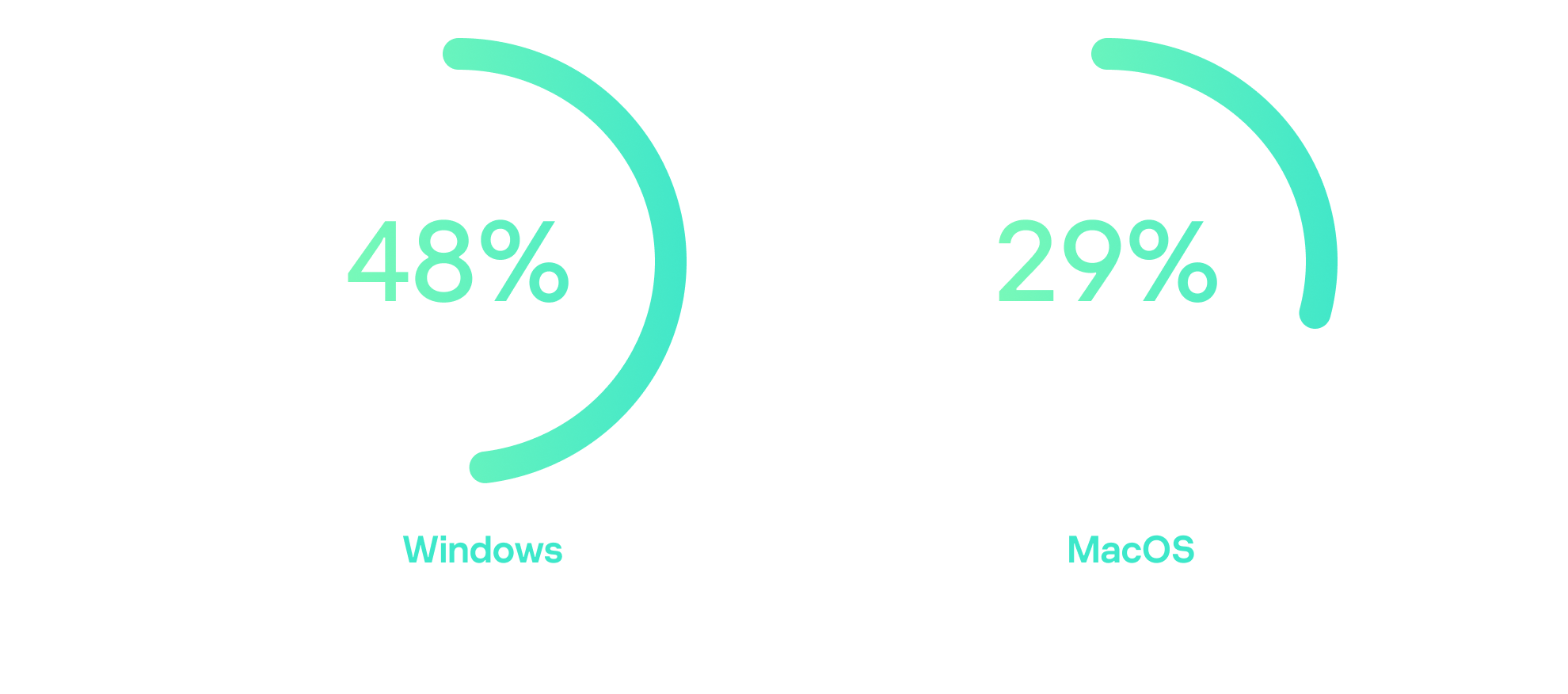
Windows remains the primary target for cyberattacks. 48% of users on Windows were targeted by different types of threats throughout 2025. For Mac users, this figure stands at 29%.
Web threats
Globally, 27% of users were attacked with web threats – these refer to malware that targets users when they are online. Web threats are not limited to online activity, but ultimately involve the internet at some stage for inflicted harm.
On-device threats
33% of users were attacked with on-device threats. These include malware that is spread via removable USB drives, CDs and DVDs, or that initially makes its way onto the computer in non-open form (for example, programs in complex installers, encrypted files, etc.).
Regional trends from 2024 to 2025 (malware detections)
24% increase in backdoors
35% increase in password stealers
64% increase in spyware
26% increase in password stealers
37% increase in spyware
1% increase in on-device threats
50% increase in backdoors
5% increase in exploits
48% increase in password stealers
64% increase in spyware
132% increase in password stealers
32% increase in spyware
2% increase in backdoors
43% increase in password stealers
53% increase in spyware
19% increase in on-device threats
25% increase in backdoors
10% increase in exploits
67% increase in password stealers
68% increase in spyware

The current cyberthreat landscape is defined by increasingly sophisticated attacks on organizations and individuals around the world. One of the most significant revelations made by Kaspersky this year was the resurgence of the Hacking Team after its 2019 rebranding, with its commercial spyware Dante used in the ForumTroll APT campaign, incorporating zero-day exploits in Chrome and Firefox browsers. Vulnerabilities remain the most popular way for attackers to get into corporate networks, followed by using stolen credentials – hence the rise in password stealers and spyware we see this year. Supply chain attacks are also common, including attacks on open-source software. This year the number of such attacks increased significantly, and we even saw the first widespread NPM worm Shai-Hulud. This increasingly complex threat landscape makes implementing robust cybersecurity strategies vital for organizations, as failure to do so can lead to months of downtime in the event of attacks. Individual users should also always use reliable security solutions, otherwise they put not only their data and money at risk, but also those of the organizations where they work.
Alexander Liskin
Head of Threat Research at Kaspersky
Recommendations
To stay protected, follow the recommendations below.
Individual users
- Do not download and install applications from untrusted sources
- Do not click on any links from unknown sources or suspicious online advertisements
- Always use two-factor authentication when available. Create strong and unique passwords, using a mix of lower-case and upper-case letters, numbers, and punctuation. Use a reliable password manager to help to remember them
- Always install updates when they become available; they contain fixes for critical security issues
- Ignore messages asking to disable security systems for office or cybersecurity software
- Use a robust security solution appropriate to your system type and devices, such as Kaspersky Premium
Organizations
- Always keep software updated on all the devices you use to prevent attackers from infiltrating your network by exploiting vulnerabilities
- Do not expose remote desktop services (such as RDP) to public networks unless absolutely necessary and always use strong passwords for them
- Use advanced Kaspersky Next security products for comprehensive visibility across all company’s corporate infrastructure to rapidly hunt out, prioritize, investigate and neutralize complex threats and APT-like attacks
- Use the latest Threat Intelligence information to stay aware of actual TTPs used by threat actors
- Back up corporate data regularly. Backups should be isolated from the network. Make sure you can quickly access the backups in an emergency if needed





 2 Dec 2025
2 Dec 2025  10 min read
10 min read