Kaspersky launches its 2025 Security Bulletin , which reviews the major cybersecurity trends of the past year and offers a look towards the future. The first KSB is dedicated to cybersecurity in the financial sector, providing an overview of major cases, key trends, and evolving threats. This year, the financial sector navigated a rapidly evolving cyber landscape, with malware spreading through messaging apps, AI-assisted attacks, supply chain compromises, and NFC-based fraud.
2025 financial sector cybersecurity in figures
8.15% of users in the finance sector faced online threats.
15.81% of users in the finance sector faced local threats.
12.8% of B2B finance sector companies faced ransomware this year (KSN Data, November 2024 through October 2025).
35.7% more unique users in the finance sector encountered ransomware detections in 2025 compared to 2023 (Nov 2024 – Oct 2025 vs Nov 2022 – Oct 2023).
1,338,357 banking trojan attacks were detected this year (November 2024 through October 2025).
Cybersecurity trends and cases shaping the financial sector in 2025
Large-scale supply chain attacks: the financial sector faced a series of unprecedented supply chain attacks, which are incidents that exploit vulnerabilities in third-party providers to reach their primary targets. The breaches demonstrated how vulnerabilities in third-party providers can cascade through national payment networks, affecting even central systems.
Organized crime converging with cybercrime: organized crime is increasingly combining physical and digital methods, creating more sophisticated and coordinated attacks. Financial institutions faced threats that blend social engineering, insider manipulation, and technical exploitation.
The Brazilian Central Bank’s reserve accounts were compromised through an intermediary. An employee allegedly sold their credentials for $2,000, enabling criminals to navigate the PIX payment ecosystem, escalate privileges, and execute fraudulent transfers. Three coordinated incidents followed: C&M Software in July ($148 million stolen), Banco Triângulo and E2 Pay in September ($5 million), and FictorPay in October ($5 million).
Old malware, new channels: cybercriminals increasingly exploit popular messaging apps to spread malware, shifting from email phishing to social channels. Banking trojans are being rewritten to use messaging platforms as a new distribution vector, enabling large-scale infections.
AI scales malware to new heights: this year, AI-enabled malware has increasingly incorporated automated propagation and evasion techniques, allowing attacks to spread faster and reach a larger number of targets. This automation also shortens the time between malware creation and deployment.
The Maverick became the first campaign demonstrating this trend. The trojan spread via malicious ZIP and LNK files on WhatsApp, showing code similarities with the previously known Coyote trojan which had been rewritten using AI-assisted generation. Infected devices automatically sent the malware to their contacts, enabling rapid, worm-like propagation. In October–November 2025, Kaspersky solutions blocked over 81,000 execution attempts worldwide.
Mobile banking attacks and NFC fraud: Android malware using ATS (Automated Transfer System) techniques automate fraudulent transactions, altering transfer amounts and recipients in real time without the user noticing. NFC-based attacks have also emerged as a key trend, enabling both physical fraud in crowded places and remote fraud via social engineering and fake apps mimicking trusted banks.
SuperCard X is an NFC relay-style malware split into two apps, with one on the victim’s phone and one for the attacker. Victims are tricked via SMiShing or calls to install the “reader” app, which captures card data for unauthorized transactions. From August 2024 to October 2025, Android malware using similar NFC techniques, including SuperCard X, were blocked over 60,000 times. Another example is the FunkSec group, which uses Rust-based malware with AI elements to combine data theft and encryption. It can disable dozens of processes, self-clean, and includes tools for DDoS attacks and password generation.
Blockchain-Based C2 Infrastructure is on the rise: crimeware attackers increasingly embed malware commands in blockchain smart contracts, targeting Web3 to steal cryptocurrencies. This method ensures persistence and makes the infrastructure extremely difficult to remove. Using blockchain for C2 operations allows attackers to maintain control even if conventional servers are shut down, highlighting a new level of resilience in cyberattacks.
Ransomware presence: these type of attacks remained a persistent threat for the financial sector across most regions this year. Worldwide 12.8% of B2B finance organizations were affected by ransomware, with 12.9% in Africa, 12.6% in Latin America, and 9.4% in Russia & CIS (KSN Data, November 2024 through October 2025).
Disappearance of certain malware families: some malware families are likely to disappear, as their activity depends directly on the operations of specific criminal groups.
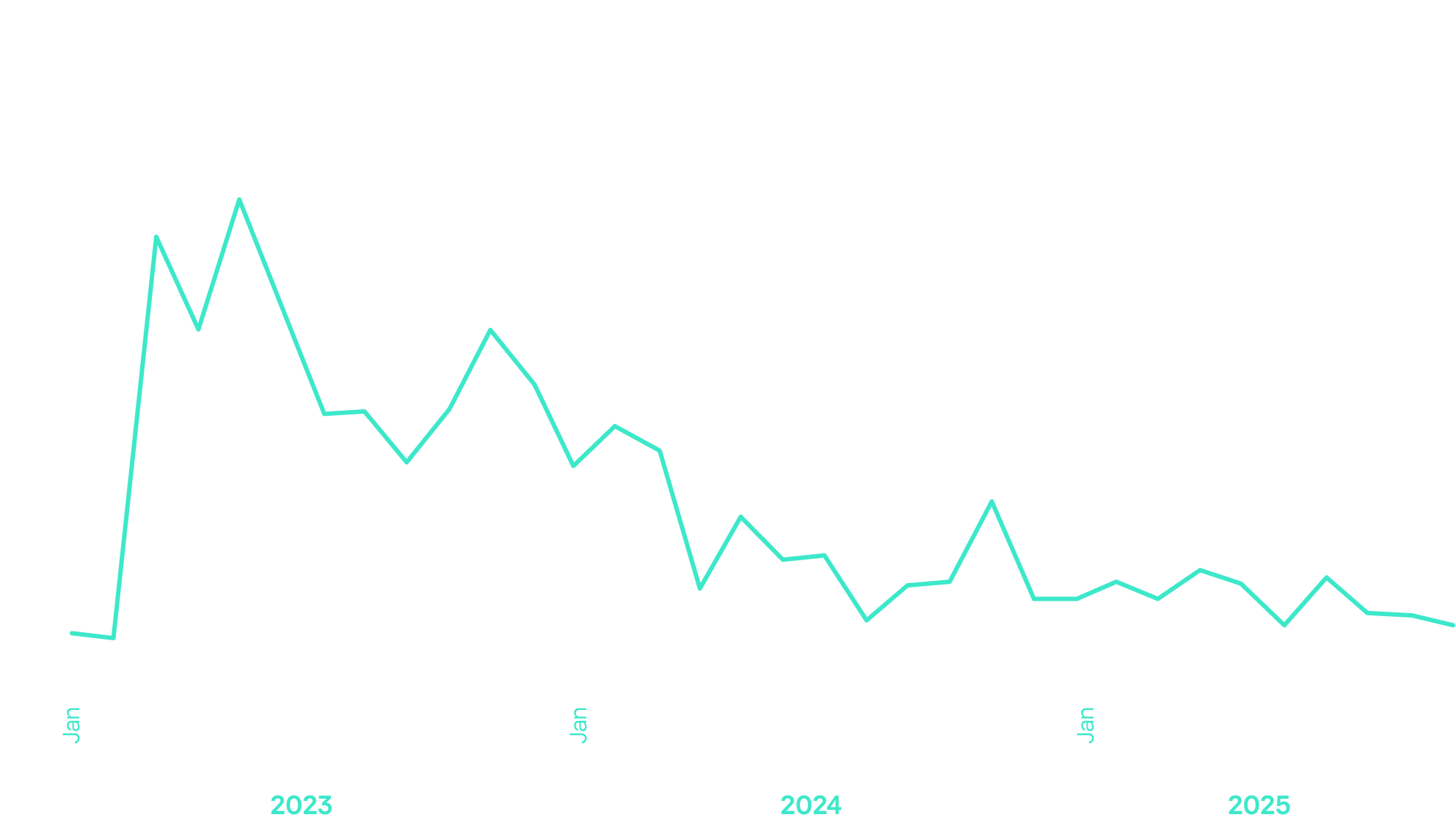

In 2025, financial cyber threats evolved into a complex landscape, with attacks hitting businesses and end users alike. Criminal groups increasingly combined digital tools, insider access, AI and blockchain to scale operations, forcing organizations to secure not only their systems but also the human networks that support them.
Fabio Assolini
Head of the Americas & Europe units at Kaspersky GReAT
Predictions: What finance cybersecurity might face in 2026
Banking Trojans will be rewritten for WhatsApp distribution: criminal groups will increasingly rewrite and scale banking trojans distribution and abuse messaging apps like WhatsApp to target corporate and government organizations that still rely on desktop-based online banking. These environments are where Windows-based banking trojans thrive.
Growth of deepfake/AI services for social engineering: the trade in realistic deepfakes and AI-powered campaigns is expected to expand even more, fueling scams around job interviews and offers, driving underground demand for tools that fully bypass KYC verification.
Appearance of regional info stealers: as Lumma, Redline and other stealers are still active, we expect to see the appearance of regional info stealers, targeting specific countries or regions, expanding the use of MaaS model.
More attacks on NFC payments: as a key technology used in payments, we’ll see more tools, more malware and attacks directed against NFC payments, in all types.
The advent of Agentic AI malware: Agentic AI malware is characterized by its ability to dynamically alter behavior mid-execution. Unlike conventional malware that relies on pre-defined instructions, agentic variants are designed to assess their environment, analyze their impact, and adapt their tactics on the fly. This means that a single piece of malware could exhibit a range of behaviors, from initial infiltration to data exfiltration or system disruption, all in response to the specific defenses and vulnerabilities it encounters.
Classic fraud will obtain new delivery: fraud will remain a major threat to end users, but its delivery methods will keep evolving. As new services and messaging platforms emerge, attackers will continue to adapt their tactics to the channels where their target audience is most active.
The persistence of ‘out of box’, pre-infected devices: the threat of counterfeit smart devices sold already infected with trojans (such as Triada) will continue to evolve. These trojans often come with extensive capabilities, including the ability to steal banking credentials, and affect not only “gray” Android smartphones but also other smart devices such as TVs.
Recommendations for users and organizations
Kaspersky experts recommend the following to keep safe:
- Download apps only from official stores and verify developer authenticity.
- Disable NFC when not in use, and utilize wallets that block unauthorized communication.
- Monitor accounts and transactions regularly for suspicious activity.
- Protect your financial transactions by adopting Kaspersky Premium with the Safe Money feature, which verifies the authenticity of known online payment systems and banking websites.
Financial organizations can embrace an ecosystem-based cybersecurity strategy that unites people, processes, and technology:
- Step 1: Assess the entire infrastructure, fix vulnerabilities, and consider external specialists for fresh perspectives that reveal concealed risks.
- Step 2: Deploy integrated platforms to monitor and control all attack vectors with rapid detection and swift response across the organization. Solutions from the Kaspersky Next product line can help with this goal, as they provide real-time protection, threat visibility, investigation, and EDR/XDR capabilities scalable to organizations of any size and in any industry.
- Step 3: Stay current with the threat landscape using Kaspersky threat intelligence and analytics, run regular awareness training to build a human firewall that recognizes threats and enforces security policies.
To learn more about our expertise in the financial sector and to find relevant solutions to mitigate risks, please visit our website.
Kaspersky Security Bulletin 2025: Decoding the Finance Sector Threats


About this talk
Explore the latest cybersecurity landscape in the financial industry with Fabio Assolini from Kaspersky's GReAT. This webinar examines the most significant security incidents, evolving threats, and technological trends from 2025 that specifically impacted financial organizations. Learn how to defend against these threats and discover strategic forecasts for 2026. Understand the critical insights from the first annual Kaspersky Security Bulletin dedicated to finance sector security.
Fabio Assolini, Head of the Americas & Europe units at Kaspersky GReAT