Statistics on attacked ICS computers in 2025
According to Kaspersky's ICS CERT quarterly threat landscape reports, in Q1 2025, the share of ICS computers attacked with malware stood at 21.9%, reflecting relative stability from late 2024. By Q2, it had dipped to 20.5%, and then in Q3 declined to around 20%. The modest 2 percentage point drop isn't indicative of a dramatic shift in attacker behavior but rather incremental defensive improvements amid evolving attack tactics.
The decrease may stem from maturing defenses outpacing attacker volume in detectable categories, though it's a fragile gain. Even at 20%, this translates to one in five ICS computers encountering a blocked threat quarterly, a stark reminder of ICS's elevated risk profile compared to general IT. It should also be noted that the decline isn't uniform – in some regions, the share of attacked ICS computers actually increased throughout the year.
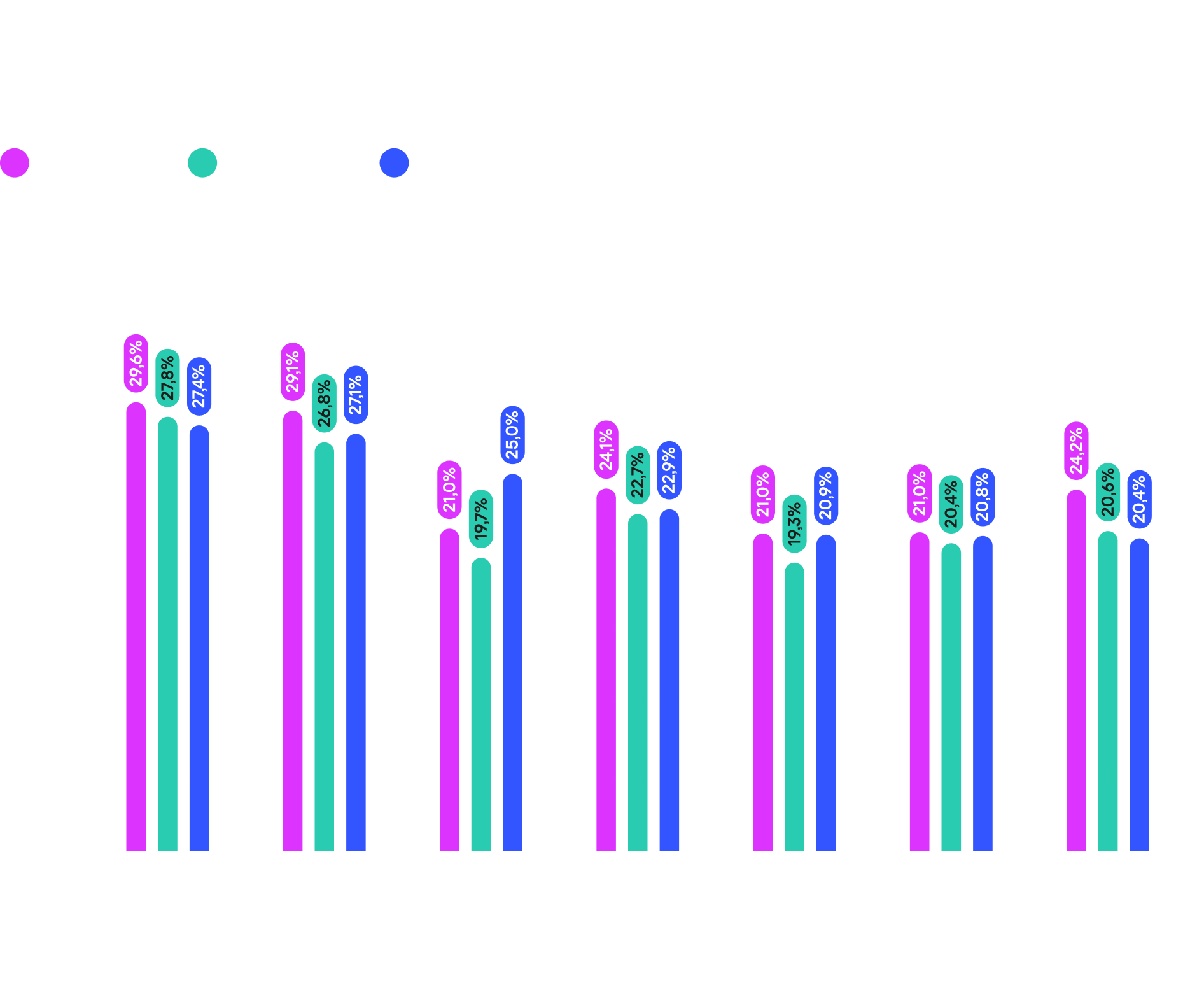
Africa, South-East Asia, East Asia, the Middle East, and South Asia are the top 5 regions with the highest share of attacked ICS computers. Africa, South-East Asia, the Middle East, Central Asia, South, West and Eastern Europe saw an increase in the share of attacked ICS computers from Q1 to Q3 2025.
Threats by industries
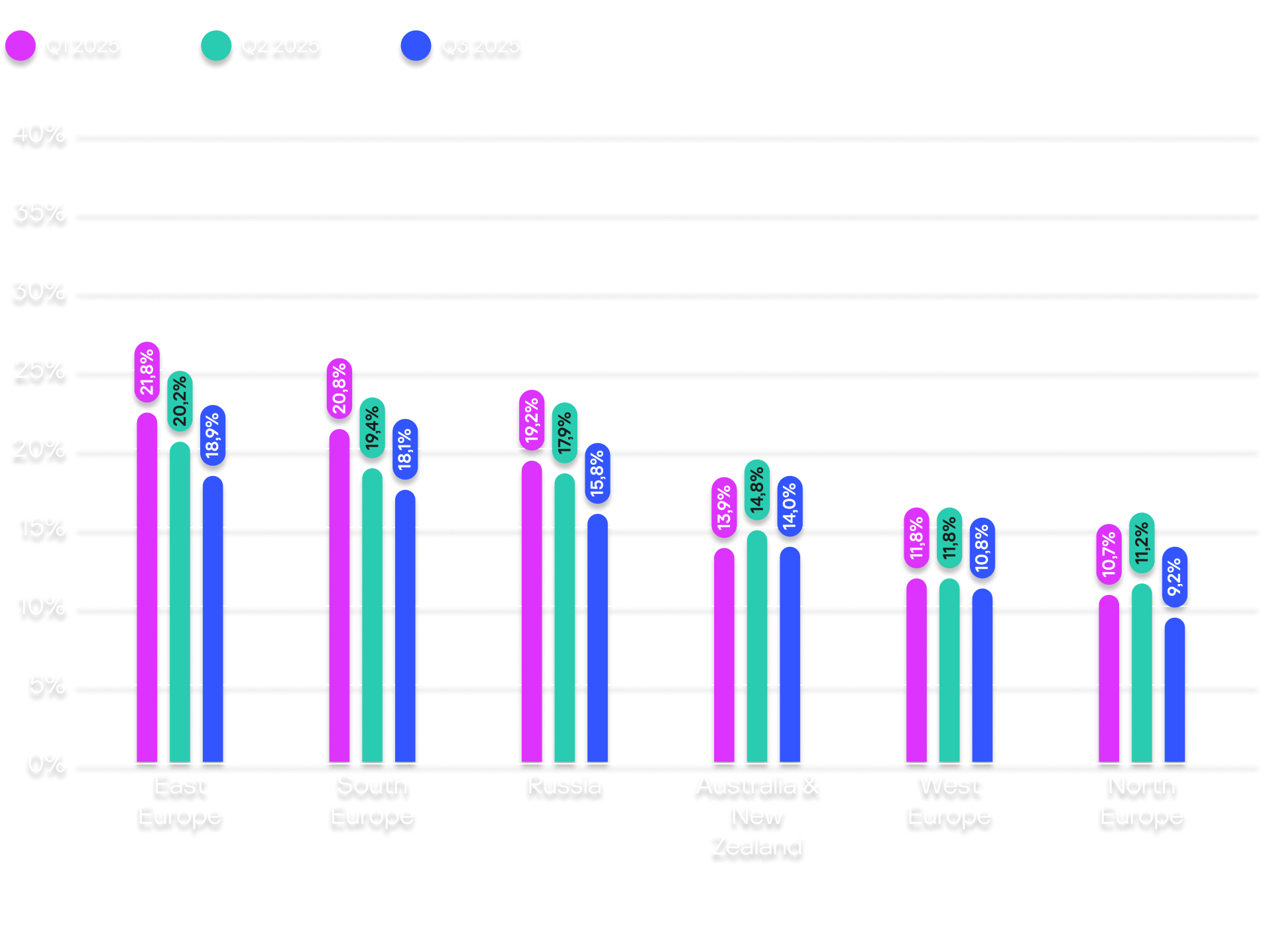
Globally, the biometrics sector led the ranking of industries and OT infrastructures by the percentage of ICS computers on which malicious objects were blocked (27.4%), followed by building automation (23.5%), electric power facilities (21,43%), construction facilities (21.1%), OT engineering and integration (21.2%), manufacturing (17.3%), and oil & gas (15.8%).
Key trends in cyberattacks on industrial organizations in 2025
Supply chain and trusted relationship exploitation
Attackers routinely exploit their potential victims’ trusted relations – for instance, contractors. This exploitation often has a technical component beyond the psychological and communicative ones, such as additional communication channels that bypass the victim’s security perimeter or are less secure. Additionally, there may be a lack of technical capability on one side to fully verify the information security status of technological components and digital artifacts provided by the other party.
- Attacks via trusted vendor weaknesses. This is especially relevant for local product vendors as they normally lack the security maturity of bigger global developers
- Attacks via trusted service providers, including those of mission-critical services, such as telecoms. The attackers primarily target the network cores of major telecommunications providers, as well as the edge routers of providers and their client organizations. They then use compromised devices and trusted relationships to compromise the networks of new victims.
AI-powered attacks
AI is being used in attacks on industrial enterprises in various ways:
- “As a pure abstraction”
In attacks on Middle Eastern organizations, bad actors in some cases used a downloader to deliver the PipeMagic backdoor (see below), which they distributed under the guise of the ChatGPT client. - “For its intended purpose”
Operators of the GLOBAL GROUP ransomware platform built an automated ransom negotiation system using AI-powered chatbots to avoid the hassle of teaching their employees English. - “Combining different AI usage approaches”
EvilAIIn disguised their malware as AI-powered productivity tools and developed it partially using an LLM, making the malicious code appear more legitimate. - “Handing over attack implementation to AI agents”
AI-agent based attacks are arising, where humans are only involved in the preparation, targeting and quality control
Attacks on Internet-facing OT network equipment
Many industrial objects, especially the remotely located ones, are actually connected to the Internet via a special-purpose OT firewall, only designed to separate communications between IT and technological networks, and most likely not designed to counter the great variety of threats that can reach them from the Internet.
Prominent regional attack cases (investigated by Kaspersky or from open sources)
Attackers used phishing emails and exploited vulnerable web applications to deploy Godzilla shell (a remote access tool), VARGEIT, and COBEACON backdoors for reconnaissance and data exfiltration. The malware leveraged multiple channels like HTTP and Outlook for command execution and network spreading. This ongoing operation since mid-2024 compromised key industrial operations, enabling persistent espionage in the region.
The backdoor constantly monitors for a “magic packet” in TCP traffic before launching a reverse shell. J-magic is a modified version of the publicly available experimental cd00r backdoor. Based on telemetry, the researchers believe that about half of the targeted devices were likely configured as a VPN gateway for their organization. The case emphasizes importance of vulnerability intelligence and vulnerability management for the border equipment of industrial enterprises.
This compromised at least 65 Windows servers belonging to educational, healthcare, insurance, transportation, retail, and IT organizations in several countries. The group signed some of its malware with a certificate issued by TrustAsia RSA Code Signing CA G3 to the developer Shenzhen Diyuan Technology Co., Ltd.
The attackers used 3 approaches to load the malware, each highlighting a particular IT/OT security problem. A loader disguised as a ChatGPT client, a Microsoft Help Index File loader that instead of reading .mshi container data contained C# code that decrypted and executed shellcode, and a DLL hijacking technique to execute the malicious library in the legitimate Google Chrome update process context.
This involved phishing emails which delivered FatalRAT Trojan via DLL sideloading (malicious libraries) and multi-stage payloads from cloud services, enabling keystroke logging and network scanning. The campaign targeted government and industrial organizations, particularly those in the manufacturing, construction, IT, telecom, healthcare, energy, and logistics and transportation sectors in Taiwan, Malaysia, China, Japan, Thailand, South Korea, Singapore, the Philippines, Vietnam, and Hong Kong. The lures used in the emails suggest that the phishing campaign targets Chinese-speaking users. Being a multinational company means you have to not only take into account cultural differences, but to also be ready for the threats specific to the country of the origin for your employees.
The Lazarus group exploited 0-day vulnerabilities in Cross Ex and Innorix Agent software via watering hole attacks (compromised trusted websites), deploying ThreatNeedle, SIGNBT, and COPPERHEDGE malware for reconnaissance. At least six organizations were hit, with payloads facilitating system compromise. This led to significant data exfiltration in high-tech industrial supply chains.
Qilin ransomware disrupted flight information displays, check-in kiosks, and baggage handling for over 10 hours, forcing manual operations. The group exfiltrated 2 TB of data amid the encryption attack. Core airport functions recovered quickly, but the incident exposed ICS vulnerabilities in aviation logistics.
Sophisticated techniques used to steal authentication data for the lateral movement stages highlight the need for industrial enterprises to continuously check their perimeter for the signs of potential compromise – such as making sure login pages have not been modified with a malicious implant and that it is still only you who is in power of controlling your companies’ DNS zone.
Email campaigns from compromised accounts used polyglot PDF/HTA (dual-format files) and PDF/ZIP files to deliver the Sosano Go backdoor (a stealth access tool) for data collection and exfiltration. The method targeted critical transportation infrastructure with obfuscated attachments. Impacts included compromises in aviation-related industrial systems, enabling potential sabotage.
Pro-Iranian actors gained initial access via stolen SSL VPN credentials (secure remote login), hosting web shells (remote command interfaces) and deploying Havoc, HanifNet, HXLibrary, NeoExpressRAT, and MeshCentral Agent for lateral movement (network spreading). Efforts focused on penetrating OT networks (physical control systems), with footholds in restricted segments. While no full OT compromises occurred, data exfiltration and persistence threatened industrial stability.
Safepay ransomware caused operational denial, leaking ~200 personal records and triggering insolvency filing. Despite the financial collapse, operations continued with secured employee wages. This case exemplified how ransomware escalates to business failure in under-resourced industrial utilities.
Attackers remotely opened the dam's water valve to full capacity for four hours using a weak default password (factory-set login) on the web control panel (online interface). This cyber-physical manipulation (digital control of machines) caused temporary denial of operations with minimal environmental damage due to low water levels. The incident revealed direct ICS interface vulnerabilities (control panel weaknesses) without needing physical access.
Polish officials confirmed to the Onet.pl news portal that an attack on an unnamed water and sewage infrastructure of a large Polish city had occurred on August 13. The attack could have left one of the country’s major cities without water, but it was prevented. The relevant services learned about the attack at the last minute and managed to shut everything down.
The company’s Halewood plant in Merseyside stopped on September 1st for more than a month (Production had restarted by October 8). A month-long denial of operations affected the company’s suppliers. Several small suppliers faced bankruptcy due to the prolonged shutdown. They were forced to suspend their own operations and send employees on leave. A group calling itself Scattered Lapsus$ Hunters took credit for the breach. The attackers said they had gained access after exploiting a vulnerability in a technology platform called SAP Netweaver (CVE-2025-31 324) highlighting high dependency of industrial enterprises on the trusted partner and service provider cybersecurity.
A ransomware attack disrupted operations at several major European airports, including Heathrow, Berlin, Brussels and Dublin, causing delays. The attack targeted ARINC cMUSE automatic check-in and boarding software provided by Collins Aerospace, a US software company owned by major defense conglomerate RTX. Airlines using the software were forced to use manual workarounds to board and check in passengers, resulting in several flights being delayed or canceled. The European Union Agency for Cybersecurity (ENISA) confirmed that the incident was a ransomware attack. Systems were eventually restored, but it highlighted supply chain risks in transportation / aviation
This attack led to disruptions to IT systems. As a result, the airline was forced to cancel flights and warned of potential disruptions to services. The cyberattack was allegedly the result of a year-long operation that penetrated Aeroflot's network, destroyed servers and gained control over employees’ personal computers.
An unknown sophisticated APT actor infected machines of high-profile organizations in Russia through update files for ViPNet software with a versatile backdoor allowing the attacker to steal files from infected computers and launch additional malicious components. This attack emphasizes high risks of supply chain attacks even via a trusted IT security provider.
Spear-phishing with password-protected archives and self-extracting installers (auto-run packages) used AnyDesk, Blat for exfiltration, and XMRig miner (crypto-mining tool), impersonating mail.ru webpages. Over a hundred targets were compromised, with a focus on industrial firms with engineering schools to steal design documents and various types of CAD/CAM- projects. The data collected during our incident response projects suggests that a single malicious person might be behind the technology espionage campaign compromising dozens of industrial enterprises.
Predictions for 2026
Incidents provoking disruptions in global logistics and international supply chains, especially in
- Energy sector
- High-tech sector
More incidents affecting non-classical targets
- Smart transportation systems. Vessels, trains, public transportation, cars and special-purpose vehicles are at risk as the protection measures are getting decades late.
- Smart buildings – for the same reason
- The same forsatellite communications
Sophisticated APT, hacktivists and ransomware gangs will be slowly moving their focus from Europe and US towards Asia, ME and Latin America following geopolitical and macro economical shifts
More of the attacks having regional nuances, including technology-wise
- Targeting local vendors and their products
- More locally-focused social engineering
Greater involvement of AI in malicious operations
- AI agents-based attacks, will become normal
- Autonomous malicious operations orchestration frameworks may arise and lower the entry barrier of mass-scale and targeted campaigns

Industrial organizations are confronting an environment where attacks are faster, smarter, and more asymmetric than ever. This year alone, we investigated campaigns like Salmon Slalom, which targeted manufacturing, telecom, and logistics firms via advanced phishing and DLL sideloading, and the Librarian Ghouls espionage operation which compromised engineering schools and industrial design environments. These attacks show that both multinational supply chains and local technical ecosystems are at risk, and every industrial enterprise must assume it is already a target and act accordingly.
Evgeny Goncharov
Head of Kaspersky ICS CERT
Recommendations
To keep OT computers protected from various threats, Kaspersky experts recommend:
- Conducting regular security assessments of OT systems to identify and eliminate possible cyber security issues.
- Establishing continuous vulnerability assessment and triage as a foundation for effective vulnerability managementprocess. Dedicated solutions like Kaspersky Industrial CyberSecurity may become an efficient assistant and a source of unique actionable information, not fully available in public.
- Performing timely updates for the key components of the enterprise’s OT network; applying security fixes and patches or implementing compensating measures as soon as it is technically possible is crucial for preventing a major incident that might cost millions due to the interruption of the production process.
- Using EDR solutions such as Kaspersky Next EDR Expert for timely detection of sophisticated threats, investigation, and effective remediation of incidents.
- Improving the response to new and advanced malicious techniques by building and strengthening teams’ skills in incident prevention, detection, and response. Dedicated OT security trainings for IT security staff and OT personnel is one of the key measures helping to achieve this.
KSB: Kaspersky ICS CERT Trends and Predictions for 2026


About this talk
In this webinar, we are taking a look at how cyberthreats in the industrial sector have evolved throughout 2025 and elaborate on what 2026 holds. Speakers will discuss per quarter ICS threat statistics, describe the industries that were most targeted in different regions, explain the most prominent attack cases, and give recommendations to organizations on how to stay secure.
Fabio Assolini, Head of the Americas & Europe units at Kaspersky GReAT
Evgeny Goncharov, Head of Kaspersky ICS CERT